Cyber security news and services
The State of Scaling Ethereum
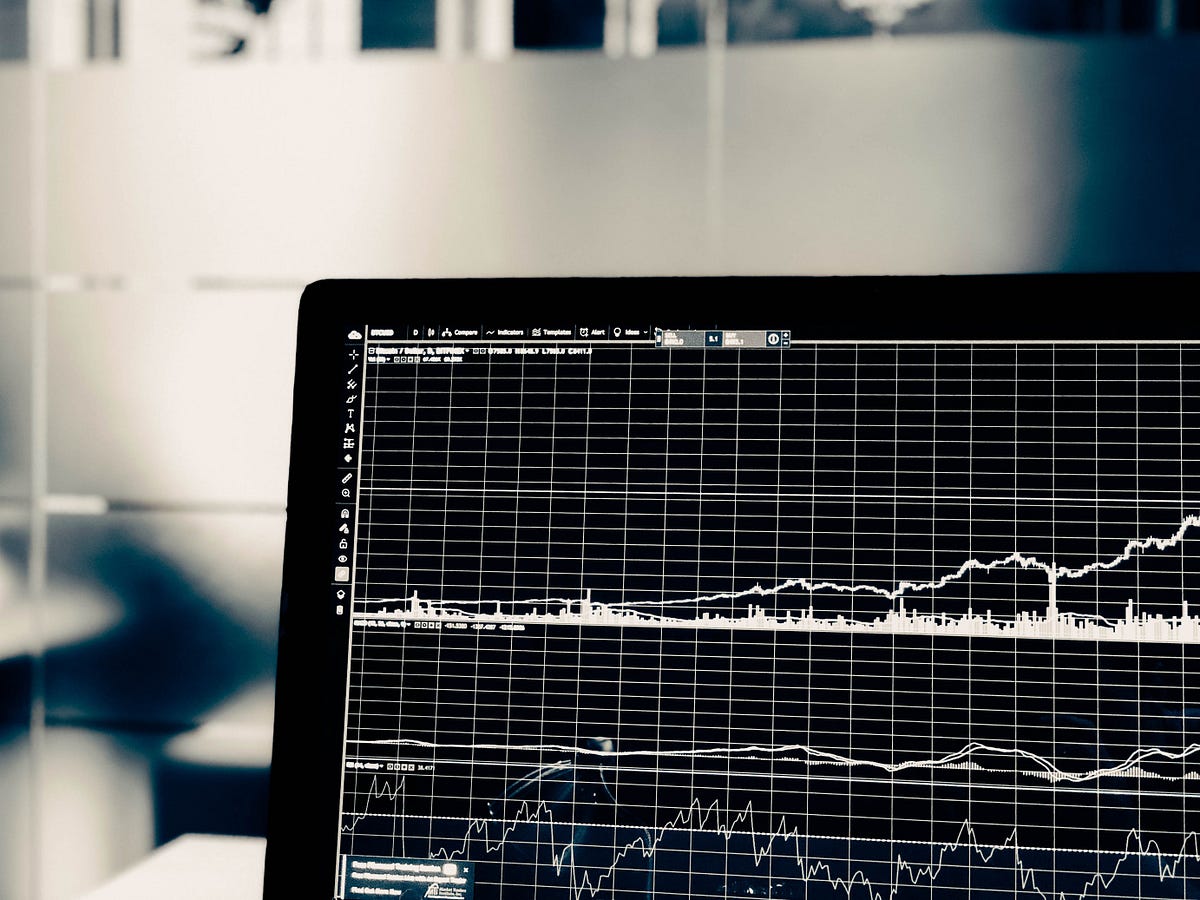
Ethereum developers have long known that scaling the network is a subject worth discussion and investment. The matter did not quite spill out from the developer community, however, until late 2017, when a decentralized application (dApp) named CryptoKitties attracted so much traffic it began slowing down the network. On top of network latency, the price of gas—the fee required to run each operation within a contract on the Ethereum blockchain—soared as users competed for their transactions to be validated.
…Critical PGP and S/MIME bugs can reveal encrypted e-mails
The Internet’s two most widely used methods for encrypting e-mail–PGP and S/Mime–are vulnerable to hacks that can reveal the plaintext of encrypted messages, a researcher warned late Sunday night. He went on to say there are no reliable fixes and to advise anyone who uses either encryption standard for sensitive communications to remove them immediately from e-mail clients. Little is publicly known about the flaws at the moment.
…Google under investigation for using Android phone data to secretly track users
THE ACCC is investigating accusations Google is using as much as $580 million worth of Australians’ phone plan data annually to secretly track their movements. Australian Competition and Consumer Commission chairman Rod Sims said he was briefed recently by US experts who had intercepted, copied and decrypted messages sent back to Google from mobiles running on the company’s Android operating system. The experts, from computer and software corporation Oracle, claim Google is draining roughly one gigabyte of mobile data monthly from Android phone users’ accounts as it snoops in the background, collecting information to help advertisers.
…Card Breach Announced at Chili’s Restaurant Chain

Malware has harvested payment card details from some Chili’s restaurants, Brinker International, the company behind the restaurant chain announced on Friday. Brinker says it detected the malware on Friday, May 11, the same day it made the announcement. The company said it is still investigating the incident together with law enforcement and third-party forensic experts.
Based on the current details it was able to gather, the company said the malware appears to have infected some of its payment systems from where it gathered credit or debit card numbers and cardholder names. The company did not publish a list of Chili’s restaurants on whose network it found the malware but said the evidence suggests the malware was only active between March and April 2018. Brinker also didn’t provide an approximate number of affected customers but promised to publish more details as the investigation goes forward.
…Internet Explorer 0-Day Discovered

Microsoft has released a patch for this vulnerability, and we strongly advise to apply it, as it is just a matter of time before other threat actors start leveraging this new opportunity in spam or exploit kit campaigns. In late April, two security companies (Qihoo360 and Kaspersky) independently discovered a zero-day for Internet Explorer (CVE-2018-8174), which was used in targeted attacks for espionage purposes. This marks two years since a zero-day has been found (CVE-2016-0189 being the latest one) in the browser that won’t die, despite efforts from Microsoft to move on to the more modern Edge.
…German online bank uses Bitcoins to transfer loans
German Radoslav Albrecht has founded an online bank that allows clients to transfer loans anywhere in the world using Bitcoin. Bitbond uses cryptocurrencies like Bitcoin to bypass the Swift international transfer system to lend money across the globe rapidly and at low cost. Clients hold the loans in digital tokens like Bitcoin only for seconds or minutes until they are exchanged back into the currency of the country where they wish to receive the funds, avoiding the crypto currencies fluctuating exchange rates.
…She didn’t see it coming: psychic arrested for $800,000 fraud

Psychic Zoe has not had a very good week. On 9 May the fortune-teller, whose real name is Ann Thompson, was arrested by the New York Police Department on suspicion of defrauding clients out of over $800,000. You’d think she might have had a premonition the police would be knocking at her door but, alas, the future isn’t always crystal clear.
…Malware Found in the Ubuntu Snap Store

Oh, snap! Just because some packages are available to install directly from the Ubuntu Software Center doesn’t make them safe. This is proved by a recent discovery of malware in some snap packages from the Ubuntu Snaps Store.
At least two of the snap packages, 2048buntu and Hextris, uploaded to the Ubuntu Snaps Store by user Nicolas Tomb, contained malware. All packages by Nicolas have since been removed from the Ubuntu Snaps Store, ‘pending further investigations’.
…CVE-2018-1000136 – Electron nodeIntegration Bypass

A few weeks ago, I came across a vulnerability that affected all current versions of Electron at the time (< 1.7.13, < 1.8.4, and < 2.0.0-beta.3). The vulnerability allowed nodeIntegration to be re-enabled, leading to the potential for remote code execution. If you’re unfamiliar with Electron, it is a popular framework that allows you to create cross-platform desktop applications using HTML, CSS, and JavaScript.
Some popular applications such as Slack, Discord, Signal, Atom, Visual Studio Code, and Github Desktop are all built using the Electron framework. You can find a list of applications built with Electron here. Electron applications are essentially web apps, which means they’re susceptible to cross-site scripting attacks through failure to correctly sanitize user-supplied input.
…Police Dept Loses 10 Months of Work to Ransomware. Gets Infected a Second Time

Secret Service agents are now investigating the point of entry for both infections, hoping to find clues and track down the hackers. The first ransomware infection took place on April 23, last month and encrypted ten months worth of work data related to active investigations. Officials said they didn’t pay the ransom and were able to recover some of the data from previous backups.
…Baltimore Police Can’t Explain Why Their All-Seeing Spy Planes Were Kept Secret

Police officials in Baltimore are trying to deflect controversy over an aerial mass-surveillance program exposed earlier this week, in which a private company quietly keeps watch over a 32-mile radius of the city by flying planes overhead for as many as 10 hours a day. Smith justified the program by alluding to two cases from the 1980s, in which the Supreme Court ruled that police don’t need a warrant to observe a suspect from above using helicopters. But those cases notably involved surveillance of a single person, not half an entire city of 621,000 people.
…Characteristics of the world’s first blockchain-smartphone revealed

Swiss startup Sirin Labs has introduced a smartphone Finney, the software component of which is based on the blockchain technology. From the technical side, Finney is not very different from other models of the higher price segment. Six-inch screen smartphone is characterized by an aspect ratio of 18: 9.
The device is based on the flagman SoC Snapdragon 845, supplemented with 6 GB of RAM and 128 GB of flash memory. The main camera has a resolution of 12 megapixels, and the front camera has an 8-megapixel resolution. The battery capacity is 3000 mAh.
…Cops Can Find the Location of Any Phone in the Country in Seconds

On Thursday, the New York Times published a blockbuster piece revealing how US law enforcement have access to a system that can geo-locate nearly any phone in the country without an officer necessarily having a court order. Now, Motherboard has obtained the letters that Senator Ron Wyden sent to the Federal Communications Commission (FCC) and telecommunications companies demanding answers on the controversial surveillance system. According to the New York Times report, a former sheriff of Mississippi County, Mo., used an obscure service called Securus to surveill targets’ cell phones, including a judge and other law enforcement officials.
…iOS 11.4 to come with 7-day USB shutout

Mobile forensics researchers recently discovered a major new security feature while poking around in the beta version of Apple’s upcoming iOS 11.4 release, due soon. It’s called USB Restricted Mode: a feature that popped up in the iOS 11.3 beta but didn’t make it to the final release. The feature snips the USB data connection over the Lightning port if the device hasn’t been unlocked for a week.
…UK cell giant EE left a critical code system exposed with a default password

EE, the largest cell network in the UK with some 30 million customers, has secured a critical code repository after a security researcher found anyone could log in with the default username and password. An anonymous security researcher, who goes by the handle Six and is founder of Project Insecurity, discovered a Sonarqube portal on an EE subdomain, which the cell giant uses to audit the code and discover vulnerabilities across its website and customer portal. But EE hadn’t changed the default password on the the downloadable portal software — ‘admin’ for both the username and password.
…Malicious Chrome extensions infect 100,000-plus users, again
The extensions were being pushed in links sent over Facebook that led people to a fake YouTube page that asked for an extension to be installed. Once installed, the extensions executed JavaScript that made the computers part of a botnet. The botnet stole Facebook and Instagram credentials and collected details from a victim’s Facebook account.
The botnet then used that pilfered information to send links to friends of the infected person. Those links pushed the same malicious extensions. If any of those friends followed the link, the whole infection process started all over again.
…Man Allegedly Used Change of Address Form to Move UPS Headquarters

Man Allegedly Used Change Of Address Form To Move UPS Headquarters To His Apartment : The Two-Way Prosecutors say he received thousands of pieces of mail intended for the company, including checks and corporate credit cards. He is now facing federal charges. Dushaun Henderson-Spruce submitted a U.S. Postal Service change of address form on Oct. 26, 2017, according to court documents.
…The source code of the TreasureHunter PoS Malware leaked online

The researchers found evidence that the threat has been around since at least late 2014.TreasureHunt was firstdiscoveredby researchers at theSANS Institute who noticed the malware generating mutex names to evade detection. TreasureHunt enumerates the processes running on the infected systemsand implement memory scraping functions to extractcredit and debit card information. Stolen payment card data are sent to C&C servers throughHTTP POST requests.
…Lawmakers move to block government from ordering digital back doors

A bipartisan group of House lawmakers have introduced legislation that would block the federal government from requiring technology companies to design devices with so-called back doors to allow law enforcement to access them. The bill represents the latest effort by lawmakers in Congress to wade into the battle between federal law enforcement officials and tech companies over encryption, which reached a boiling point in 2015 as the FBI tussled with Apple over a locked iPhone linked to the San Bernardino terror attack case.
…Vigilante Hacks Government-Linked Cyberespionage Group

Somewhere, government-linked hackers might be panicking. A digital vigilante has struck back against what researchers believe is a cyberespionage group connected to a nation state. The hacker has allegedly stolen, rather ironically, a cache of data that the government-linked hackers lifted from their own victims across the Middle East.
The news provides a rare instance of someone targeting a so-called advanced persistent threat, or APT, as well as an opportunity for a behind-the-scenes look at a government hacking campaign. “10 minutes of effort; intel on Iranian APTs,” the anonymous hacker told Motherboard in an online chat, saying which nation they believe may be linked to the hacking group. Some cybersecurity experts tentatively agreed.
…