Cyber security news and services
Warriors’ Steph Curry will auction off celebrity CryptoKitties

CryptoKitties took off with its cute blockchain-based collectible kittens last fall. Now, it is bringing sports celebrities into mix, starting with collectibles from Golden State Warriors’ star basketball player Stephen Curry. The first-ever celebrity-branded CryptoKitty will go up for auction today.
CryptoKitties became a sensation after it debuted in November as a collectible game built on top of a blockchain and the Ethereum cryptocurrency. In March, the CryptoKitties maker, Axiom Zen game studio, spun out as a separate company and raised $12 million in funding from Andreessen Horowitz and Union Square Ventures. The Curry kitties will probably draw a lot of attention.
…Uhh, Google Assistant Impersonating a Human on the Phone Is Scary as Hell to Me
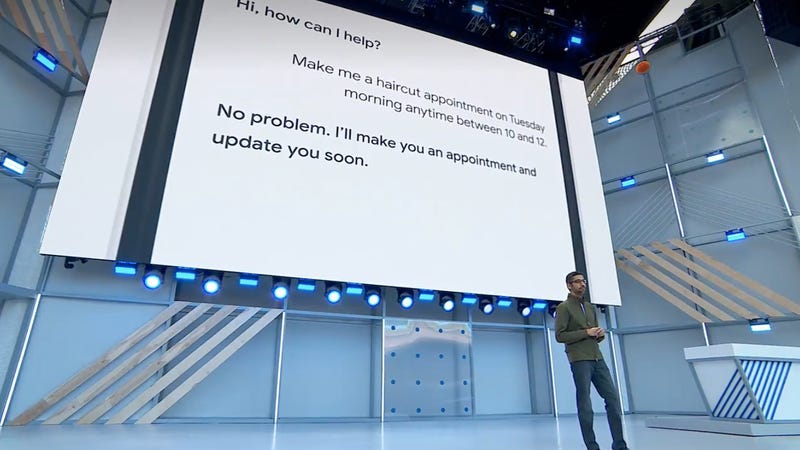
The near future terror of this project has to do with how it could be used to further erode your privacy and security. Google has access to a lot of your information. It knows everything you browse on Chrome, and places you go on Google Maps.
If you’ve got an Android device it knows who you call. If you use Gmail it knows how regularly you skip chain emails from your mom. Giving an AI that pretends to be human access to all that information should terrify you.
…Critical vulnerability impacts Bitcoin Cash miners

On Monday, Bitcoin ABC said in a security advisory that a critical vulnerability has been found in Bitcoin ABC version 0.17.0 which has the potential to cause an unintended split in the Bitcoin Cash network. In order to exploit the vulnerability, an attacker would need to construct a malicious transaction which could be accepted into Bitcoin ABC and consequently mined into a block. Once this block has been established, the block would then reject all other versions of Bitcoin Cash compliant implementations.
…Equifax reveals full horror of its data breach

Equifax has published yet more detail on the data lost in its now-infamous 2017 data breach. 146.6 million names, 146.6 million dates of birth, 145.5 million social security numbers, 99 million address information and 209,000 payment cards (number and expiry date) breached, the company says, there were also 38,000 US drivers’ licenses and 3,200 passport details.
Source: co.uk
…UK police say 92-percent false positive facial recognition is no big deal

New data about the South Wales Police’s use of the technology obtained by Wired UK and The Guardian through a public records request shows that of the 2,470 alerts from the facial recognition system, 2,297 were false positives. In other words, nine out of 10 times, the system erroneously flagged someone as being suspicious or worthy of arrest.
…Hundreds of big-name sites hacked, converted into drive-by currency miners
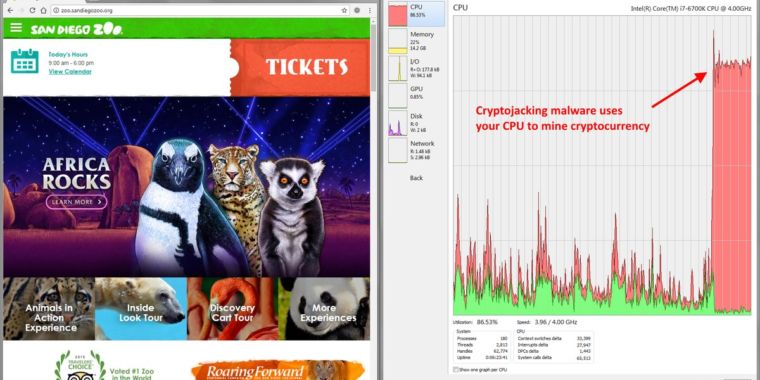
A mass hacking campaign that targets a critical vulnerability in the Drupal content management system has converted more than 400 government, corporate, and university websites into cryptocurrency mining platforms that surreptitiously drain visitors’ computers of electricity and computing resources, a security researcher said Monday. Sites that were hacked included those belonging to computer maker Lenovo, the University of California at Los Angeles, the US National Labor Relations Board, the Arizona Board of Behavioral Health Examiners, and the city of Marion, Ohio, Troy Mursch, an independent security researcher, told Ars on Monday. The Social Security Institute of the State of Mexico and Municipalities, the Turkish Revenue Administration, and Peru’s Project Improvement of Higher Education Quality were also affected.
…Op-ed: Ray Ozzie’s crypto proposal—a dose of technical reality

In the debate over law enforcement access to encrypted devices, technical details matter. The rhetoric has been stark and, dismayingly often, divorced from technical reality. For example, two years ago we were told that only Apple could write software to open the phone of the San Bernardino terrorist; the technical reality turned out to be that an FBI contractor was able to do so.
…Even Privacy Advocates Are Tracking You Online
Its website, CAPrivacy.org, is pretty much what you’d expect. There are creepy fictional videos portraying people’s birth date, physical location, and potentially embarrassing info about their online purchases (hair loss prevention shampoo) and the apps they use (online poker). Below the videos, there’s a motivating message: “It’s your personal information.
Take back control!” There is one surprising aspect, though. Each time someone visits, software gleans what information it can about her, then sends that information to Facebook, including her IP address, what web pages she was on before and after visiting, and so on.
…SynAck targeted ransomware uses the Doppelgänging technique
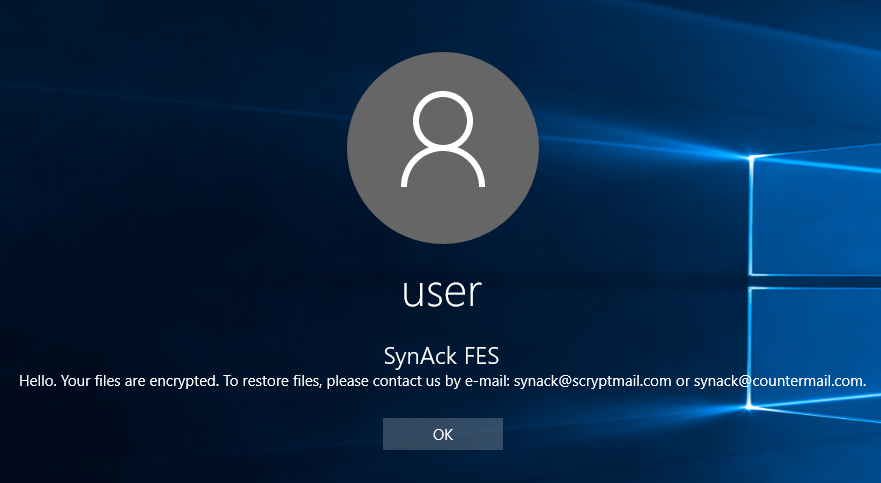
The Process Doppelgänging technique was first presented in December 2017 at the BlackHat conference. Since the presentation several threat actors have started using this sophisticated technique in an attempt to bypass modern security solutions. In April 2018, we spotted the first ransomware employing this bypass technique – SynAck ransomware.
It should be noted that SynAck is not new – it has been known since at least September 2017 – but a recently discovered sample caught our attention after it was found to be using Process Doppelgänging. Here we present the results of our investigation of this new SynAck variant.
…Ticketmaster to trial facial recognition technology at live venues

The company suggested a number of other ways it may use the technology, including to serve more personalized offers and product tie-ins while attendees move around the venue. It would also allow for “development of deeper customer relationships” between fans, artists, venues, and teams. Moreover, Ticketmaster touts the technology as boosting safety and security, as it allows venues to know exactly who is in attendance — though an e-ticket tied to an individual’s mobile device would presumably offer a similar benefit.
…That New Memory Smell: Tech Can Tell if Your Flash is New or Recycled

Flash is designed to last a decade or more of use. A lot of the gadgets that rely on it are not. Shady recyclers have spotted opportunity in that mismatch, stripping out used chips and selling them as new.
But engineers at the University of Alabama have come up with a straightforward electronic examination that can tell if a flash chip is new or recycled, even if that chip has only seen 5 percent or less of its life. And the technique is so straightforward that a smartphone app could run it on its own memory.
…Researchers link a decade of potent hacks to Chinese intelligence group
Researchers said Chinese intelligence officers are behind almost a decade’s worth of network intrusions that use advanced malware to penetrate software and gaming companies in the US, Europe, Russia, and elsewhere. The hackers have struck as recently as March in a campaign that used phishing emails in an attempt to access corporate-sensitive Office 365 and Gmail accounts. In the process, they made serious operational security errors that revealed key information about their targets and possible location.
…Idaho State University Lost Enough Weapons-Grade Plutonium to Make a Dirty Bomb
On Friday, the Nuclear Regulatory Commission announced that Idaho State University may face an $8,500 fine after losing one gram of weapons-grade plutonium. Although this quarter-sized amount of plutonium is nowhere near enough to make a nuclear weapon, it is enough to make a dirty bomb that spreads radiation, according to the Associated Press.
Source: vice.com
…Telegram’s billion-dollar ICO has become a mess

The company recently canceled the public sale piece of its ICO, the Wall Street Journal reported this week, after it raised $1.7 billion from private sale investors, according to SEC filings. But the issues date back further.
Source: techcrunch.com
…Half a million pacemakers need a security patch

The US Food and Drug Administration (FDA) last month approved a firmware patch for pacemakers made by Abbott’s (formerly St Jude Medical) that are vulnerable to cybersecurity attacks and which are at risk of sudden battery loss.
Source: sophos.com
…Internet Shortcut used in Necurs malspam campaign

This attack relies on the file:// protocol to load and execute a remote script from a samba (SMB) share. This is noteworthy because typically the attachment is used as a downloader, but instead here we see one additional step that pushes this function one degree further thanks to the .url shortcut.
Source: malwarebytes.com
…Australia’s Commonwealth Bank lost 20 Million customer records

According to thebroadcaster ABC, the data were supposed to have been destroyed when a sub-contractor after the dismantled a data centre. The sub-contractor did not provide the bank the documentation to confirm this the disruption of the magnetic data tapes, anyway the bank tried to downplay the situation confirming that the records don’t include passwords, PINs or other financial or sensitive information.
…MassMiner Takes a Kitchen-Sink Approach to Cryptomining

Once the malware has been installed, it sets about mining for Monero and hooking up with a crypto-wallet and mining pool; it also connects with its C2 server for updates, and configures itself to infect other machines on the network. Meanwhile, a short VisualBasic script is used to deploy the malware to compromised Apache Struts servers, and it moves laterally by replicating itself like a worm. MassScan meanwhile passes a list of both private and public IP ranges to scan during execution, to find fresh server targets out on the web that it can break into with the SQLck brute-force tool.
…Twitter: You Should Change Your Twitter Password
If you use the same password for multiple services (please don’t do that), or have your Twitter account connected to other login credentials online, you should change these passwords immediately. The logs that exposed users’ passwords were internal, but if anyone could see them at all the safest thing to do is change them.
Source: vice.com
…eBay, Organized Crime, and Evangelical Christians: The Ethical Minefield of Studying Ancient Civilizations

The artifacts were smuggled into the United States beginning in 2010, near the end of the Iraq War—falsely labeled as tile samples, and eventually intercepted by Customs and Border Protection. Hobby Lobby agreed to surrender them last year, forfeiting an additional $3 million, after a civil complaint was filed in the US District Court for the Eastern District of New York.
…