Cyber security news and services
Google+ bug exposes non-public profile data for 52 million users

Two months after disclosing an error that exposed the private profile data of almost 500,000 Google+ users, Google on Monday revealed a new leak that affects more than 52 million people. The programming interface bug allowed developers to access names, ages, email addresses, occupations, and a wealth of other personal details even when they were set to be nonpublic. The bug was introduced in a release that went live at an undisclosed date in November and was fixed a week later, Google officials said in a blog post.
…Millions of smartphones were taken offline by an expired certificate

Ericsson has confirmed that a fault with its software was the source of yesterday’s massive network outage, which took millions of smartphones offline across the UK and Japan and created issues in almost a dozen countries. In a statement, Ericsson said that the root cause was an expired certificate, and that ‘the faulty software that has caused these issues is being decommissioned.’ The statement notes that network services were restored to most customers on Thursday, while UK operator O2 said that its 4G network was back up as of early Friday morning.
…Bitcoin Options Bought for $1 Million Will Soon Be Worthless

Purchased for almost $1 million on LedgerX’s trading platform just days after Bitcoin peaked a year ago, the call options have a strike price of $50,000 and an expiry date of Dec. 28, 2018. For the contracts to retain any value at expiry, Bitcoin would need to rally more than 1,400 percent. The options’ almost certain wipeout is a less-than-ideal outcome for the buyer, but it may not be quite as bad as it seems.
…Malicious sites abuse 11-year-old Firefox bug that Mozilla failed to fix

This wouldn’t be a big deal, as the web is fraught with this kind of malicious sites, but these websites aren’t abusing some new never-before-seen trick, but a Firefox bug that Mozilla engineers appear to have failed to fix in the 11 years ever since it was first reported back in April 2007. The bug narrows down to a malicious website embedding an iframe inside their source code. The iframe makes an HTTP authentication request on another domain.
…The biggest crypto programming errors of all time

One small crypto programming error can lead to millions in lost funds. As you are about to learn, a bug in your code can equal disaster on the blockchain. These far-reaching consequences are all the more reason to make your project open-source.
Open-source projects gain added security because of the large number of developers checking the code for errors. That being said, even open-source projects contain programming mistakes. Let’s take a moment to examine the five biggest crypto programming errors in history.
…Confidential transactions have arrived, a dive into the AZTEC Protocol

Transaction privacy is a fundamental requirement for many kinds of financial services, and the inability to provide this privacy has prevented Ethereum from providing compelling alternatives to traditional financial instruments. There are several blockchains and blockchain projects that use cryptographic techniques to provide this privacy, but this privacy is reserved for the ‘native’ cryptocurrency of the blockchain in question. This transaction privacy is not accessible for digital assets built on top of blockchain protocols.
…How Criminals Steal $37 Billion a Year from America’s Elderly

Telephone pitchers, online scammers and even family members target the most vulnerable among us. And it’s about to get worse. Marjorie Jones trusted the man who called to tell her she’d won a sweepstakes prize, saying she could collect the winnings once she paid the taxes and fees.
After she wired the first payment, he and other callers kept adding conditions to convince her to send more money. As the scheme progressed, Jones, who was legally blind and lived alone in a two-story house in Moss Bluff, Louisiana, depleted her savings, took out a reverse mortgageand cashed in a life insurance policy. She didn’t tell her family, not even the sister who lived next door.
…Kubernetes’ first major security hole discovered

Kubernetes has become the most popular cloud container orchestration system by far, so it was only a matter of time until its first major security hole was discovered. And the bug, CVE-2018-1002105, aka the Kubernetes privilege escalation flaw, is a doozy. It’s a CVSS 9.8 critical security hole.
CVSS 9.8 critical security hole. With a specially crafted network request, any user can establish a connection through the Kubernetes application programming interface (API) server to a backend server. Once established, an attacker can send arbitrary requests over the network connection directly to that backend.
…How I Dumped eBay Japan’s Website Source Code
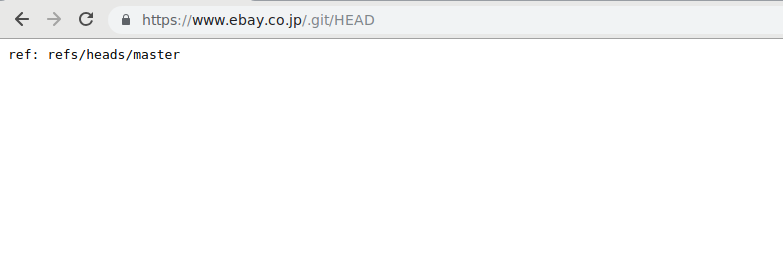
Today I wanna write about a finding I discovered during a research project where the aim was to find critical vulnerabilities in Alexa Top 1 Million websites. The main focus was to discover common configuration issues which do not require sophisticated exploits, which are easy to find and which can have a high impact on businesses. Some results of this research were presented at ITSECX 2018, an Austrian IT-Security conference.
…The FBI Created a Fake FedEx Website to Unmask a Cybercriminal

The FBI has started deploying its own hacking techniques to identify financially-driven cybercriminals, according to court documents unearthed by Motherboard. The news signals an expansion of the FBI’s use of tools usually reserved for cases such as child pornography and bomb threats. But it also ushers in a potential normalization of this technologically-driven approach, as criminal suspects continually cover up their digital trail and law enforcement have to turn to more novel solutions.
…Why x86 won’t survive

Why x86 won’tsurvivex86 is a micro-architecture created by Intel that has been around since 1978. It powers most laptops, and more than likely powers the one you’re using right now. It’s considered powerful, effective, and reliable… until a few months ago.
A short history of leaks and exploits found in the x86 micro-architecture found in 2018 alone:- Meltdown,- Spectre,- SMT/Hyper threading found to be a security threat. Seems like a small amount, right? No.
…Secret Service cracks down on credit card skimming at gas pumps nationwide

Secret Service cracks down on credit card skimming at gas pumps nationwide The agency recovers about 20 to 30 skimmers a week, with the average skimmer having information from about 80 cards on it, according to one agent. The U.S. Secret Service said it is kicking off the holiday season with a nationwide initiative to crack down on credit card skimming devices installed at gas stations. The operation, called “Operation Deep Impact,” was launched on Thanksgiving Day and is set to coincide with an increased demand for fuel over the holidays.
…Google is tracking you. Even when you’re in Airplane Mode
Google is tracking you. Even when you’re in Airplane Mode. It knows when you get out the car.
When you’re walking. We now have proof. Google has been secretly tracking people against their wishes.
The company has been collecting Android users’ location data, even when they’ve actively disabled location services. It’s an extremely concerning discovery, which means that Google can pinpoint exactly where you are even when you go out of your way to hide this information.
…German eID Authentication Flaw Lets You Change Identity
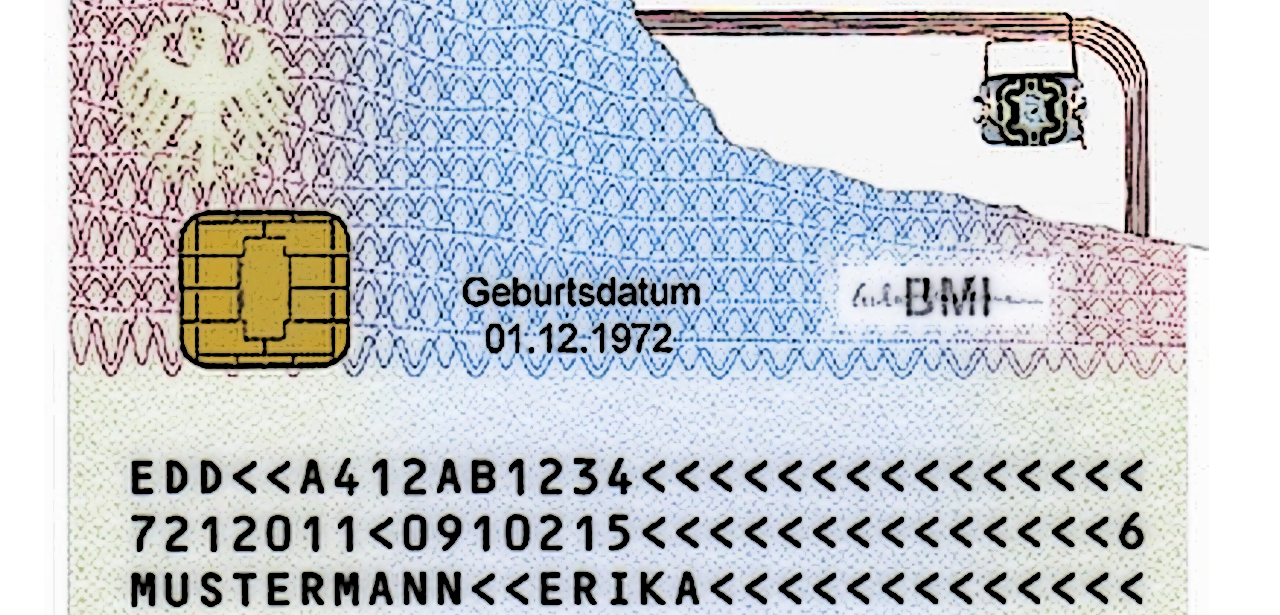
German identity cards issued since 2010 come with a radio frequency identification chip that stores information about the holder. This includes name, date of birth and a biometric picture. If the holder so chooses, it can also store their fingerprints.
The new cards are machine-readable and can be used as travel documents in most countries in Europe, as well as for authentication into online government services (tax, mail) or for age verification. Authentication via the RFID chip is possible using a smartcard reader and an eID client application that communicates with the RFID chip and an authentication server to validate the login data. To prevent tampering with the ID card data, the authentication server checks the validity of the information and then signs its reply, so that the web service can trust the legitimacy of the data received.
…CDC: Outbreak of E. coli Infections Linked to Romaine Lettuce
CDC is advising that U.S. consumers not eat any romaine lettuce, and retailers and restaurants not serve or sell any, until we learn more about the outbreak. This investigation is ongoing and the advice will be updated as more information is available. Consumers who have any type of romaine lettuce in their home should not eat it and should throw it away, even if some of it was eaten and no one has gotten sick.
…France is ditching Google to reclaim its online independence

Snowden and Cambridge Analytica have put France off Silicon Valley giants. It’s a change of heart that could have global ramifications France is working hard to avoid becoming a digital colony of the US or China. Last month, both the French National Assembly and the French Army Ministry declared that their digital devices would stop using Google as their default search engines.
…The dark side of YouTube
The YouTube algorithm that I helped build in 2011 still recommends the flat earth theory by the hundreds of millions. This investigation by @RawStory shows some of the real-life consequences of this badly designed AI.
Source: threader.app
…Hacker Say They Compromised ProtonMail. ProtonMail Says It’s BS.

According to the message, a hacker going by the name AmFearLiathMormakes quite a few interesting claims such as hacking ProtonMail’sservices and stealing user’s email, that ProtonMail is sending their user’s decrypted data to American servers, and that ProtonMail is abusing the lack of Subresource Integrity (SRI) use to purposely and maliciously steal their user’s passwords.
Source: bleepingcomputer.com
…‘Crypto hangover’ hammers Nvidia’s outlook, shares drop 17 percent
Chip designer Nvidia Corp on Thursday forecast disappointing sales for the holiday quarter, pinning the blame on unsold chips piling up with distributors and retailers after the evaporation of the cryptocurrency mining boom. The Santa Clara, California-based company also posted sales that missed expectations for its third quarter. Shares plunged nearly 17 percent in late trading to $168.32.
For decades, Nvidia has supplied gaming cards to boost computer graphics, but in recent years cryptocurrency miners adopted the company’s cards to turn bits into wealth.
…A 100,000-router botnet is feeding on a 5-year-old UPnP bug in Broadcom chips

A recently discovered botnet has taken control of an eye-popping 100,000 home and small-office routers made from a range of manufacturers, mainly by exploiting a critical vulnerability that has remained unaddressed on infected devices more than five years after it came to light. Researchers from Netlab 360, who reported the mass infection late last week, have dubbed the botnet BCMUPnP_Hunter. The name is a reference to a buggy implementation of the Universal Plug and Play protocol built into Broadcom chipsets used in vulnerable devices.
…