Cyber security news and services
Nakamoto Family Foundation

Announcing the first excerpt to a literary work consisting of two parts. The excerpt is provided. I wanted to include it as a brief glimpse of history.
Even for those that can’t read the full book, I wanted to make this available to everyone. A short story if you will, with some of the most brought up questions and answers. I wanted the people and the facts to be known.
…DNS Poisoning or BGP Hijacking Suspected Behind Trezor Wallet Phishing Incident
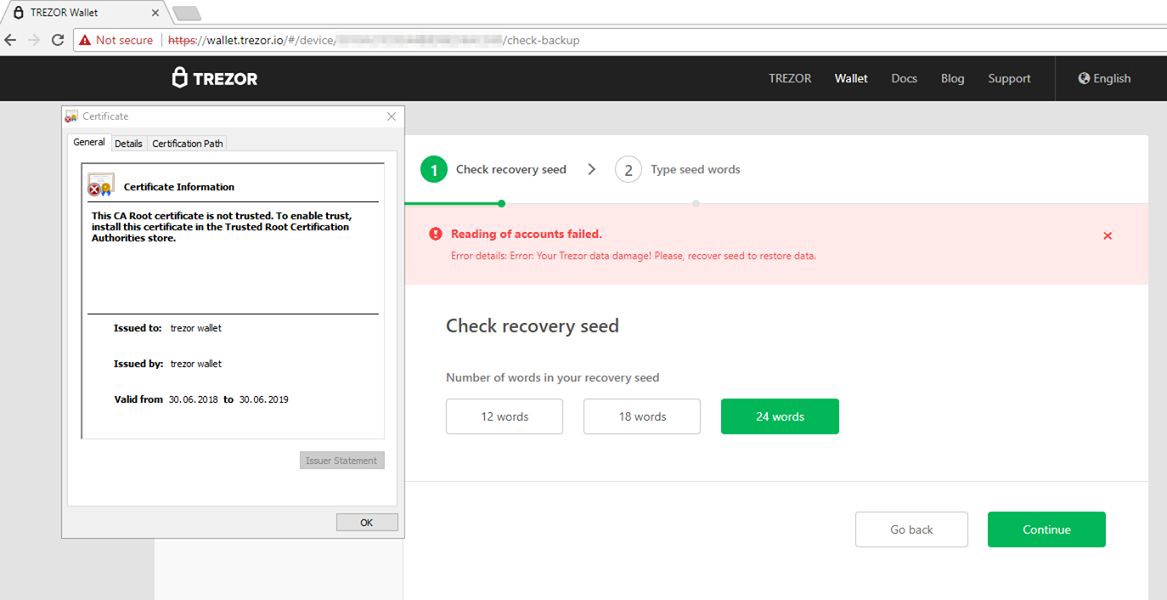
The Trezor team says ‘signs point toward DNS poisoning or BGP hijacking’ as the means attackers hijacked legitimate traffic meant for the official wallet.trezor.io domain but redirected these users to a malicious server hosting a fake website. An investigation is still underway to determine the exact cause. The incident came to light after users complained that they encountered an invalid HTTPS certificate when landing on Trezor’s web wallet portal.
…New RAMpage exploit revives Rowhammer attack to root Android devices
In late 2016, Google’s security team scrambled to fix a critical vulnerability that allowed attackers to gain unfettered root access to Android devices by using a relatively new class of exploit that manipulates data stored in memory chips. Now, 21 months later, many of the same researchers behind the attack, dubbed Drammer, are back to say that a large number of Android phones and tablets remain vulnerable to the rooting attacks because the patches Google deployed weren’t adequate. The original Rowhammer attack against PCs made it possible for an untrusted computer application to gain nearly unfettered system privileges or to bypass security sandboxes designed to keep malicious code from accessing sensitive operating system resources.
…Samsung phones are spontaneously texting users’ photos to random contacts without their permission

Bad news for Samsung phone owners: some devices are randomly sending your camera roll photos to your contacts without permission. As first spotted by Gizmodo, users are complaining about the issue on Reddit and the company’s official forums. One user says his phone sent all his photos to his girlfriend.
The messages are being sent through Samsung’s default texting app Samsung Messages. According to reports, the Messages app does not even show users that files have been sent; many just find out after they get a response from the recipient of the random photos sent to them. A Samsung spokesperson tells The Verge it’s “aware of the reports” and that its technical teams are “looking into it.”
…$5.2 Million in Cryptocurrency Seized in EU’s Largest LSD Raid

European law enforcement agencies dismantled a Darknet drug trafficking network, seizing almost 800,000 doses of LSD and over $5 million in Bitcoin, IOTA, and Lumens. Ulbricht, better known by his deep web pseudonym, “Dread Pirate Roberts,” was charged with narcotics trafficking, computer hacking, and money laundering after his arrest at the Glen Park Branch Library in San Francisco on October 1, 2013. The FBI seized 144,336 Bitcoins during the Silk Road bust, which they auctioned for a meager $48 million.
…Feds Pose as Cryptocurrency Money Launderer to Bust Alleged Dark Web Dealers

In a novel investigative strategy, rather than just following the money, investigators went undercover as someone converting Bitcoin into cash, exploiting a financial bottleneck faced by dark web criminals. Law enforcement agencies are always looking for new ways to identify suspects on the dark web, whether that means using malware to unmask people, executing wide ranging attacks on the Tor anonymity network, or tracking a drug dealer’s physically mailed packages. But on Wednesday, the Department of Justice announced dozens of dark web arrests thanks to a relatively novel technique.
…Facebook lifts crypto ban amid rumours of Coinbase acquisition

The lifting of the ban – put in place in January amidfears that ads were used for fraud –was welcomed by industry figures, with some saying that itindicated the firm’s recognition of the potential of bitcoin and other cryptocurrencies. But perhaps more significant than the immediate implications for cryptocurrency firms is what the movesignals about Facebook’s own ambitions. Last month, the social network announced its biggest ever management reshuffle, which included the launch of an exploratory blockchain group that reports directly to the company’s CTO, Mike Schroepfer.
…Ticketmaster breached for months, personal data stolen by hackers

Ticketmaster has warned customers that their personal information may have been compromised, after malicious code was discovered running on its website. Up to 40,000 UK customers who purchased, or attempted to purchase, tickets between February and June 23, 2018 are thought to be affected. In addition, international customers who purchased, or attempted to purchase, tickets between September 2017 and June 23, 2018 may also be at risk.
…Cryptocurrency Transactions May Uncover Sales of Shadow Broker Hacking Tools

In 2016, a group of self-described hackers started releasing a steady stream of code stolen from the NSA. As well as dumping some hacking tools publicly, such as exploits that were later incorporated into the crippling WannaCry ransomware attack, the so-called Shadow Brokers also listed more tools on a dedicated online shop and a “monthly dump service” to access additional code. A team of University College London (UCL) researchers recently found likely evidence of payments for those alleged exploits by examining transactions in Zcash, a privacy-focused cryptocurrency that the Shadow Brokers asked potential customers to use, and traced the movement of some of the coins to a specific cryptocurrency exchange.
…California Unanimously Passes Historic Privacy Bill

California lawmakers unanimously passed a new privacy bill on Thursday that would give residents of the state more control over the information businesses collect on them and impose new penalties on businesses that don’t comply. It is the first law of its kind in the United States. The so-called California Consumer Privacy Act of 2018 (AB 375) was introduced late last week by state assemblymember Ed Chau and state senator Robert Hertzberg, in a rush to defeat a stricter privacy-focused ballot initiative that had garnered more than 600,000 signatures from Californians.
…Facebook patent would turn your mic on to analyze how you watch ads
Further ReadingFacebook’s Cambridge Analytica scandal, explained [Updated]As Facebook tries to get ahead of public pressure about what the service does and doesn’t track about its users, a patent application has emerged which would enable something that the service’s detractors have long theorized and feared: silently triggered microphones that keep tabs on Facebook users. The patent, filed by Facebook in December 2016 and published on June 14 (PDF), emerged this week thanks to its discovery by UK publication Metro. The patent’s language revolves specifically around advertisements—Facebook’s biggest cash cow—and how a device with an installed app could be triggered by a vague ‘activation module’ to turn on its microphone and listen to how those ads play out in an average home.
…A new data breach may have exposed personal information of almost every American adult

A little-known Florida company may have exposed the personal data of nearly every American adult, according to a new report. Wired reported Wednesday that Exactis, a Palm Coast, Fla.-based marketing and data-aggregation company, had exposed a database containing almost 2 terabytes of data, containing nearly 340 million individual records, on a public server. That included records of 230 million consumers and 110 million businesses.
…PROPagate Code Injection Technique Detected in the Wild for the First Time
PROPagate is a relatively new code injection technique discovered last November. Back then, a security researcher found that an attacker could abuse the SetWindowSubclass API, a function of the Windows operating system that manages GUIs, to load and execute malicious code inside the processes of legitimate apps. The infosec research community deemed the technique innovative, similar in creativity to the AtomBombing technique, albeit both different in their own right.
…File-Wiping Malware Placed Inside Gentoo Linux Code After GitHub Account Hack

An unknown hacker has temporarily taken control over the GitHub account of the Gentoo Linux organization and embedded malicious code inside the operating system’s distributions that would delete user files. Thankfully, the malicious code fails to trigger properly and users’ files remain safe. How the hacker gained access to Gentoo’s GitHub account still remains a mystery, but since announcing the hack late last night, the Gentoo team says it regained control over their account, albeit their profile remained offline at the time of this article’s publication.
…Adidas Announces Data Breach

The company says it became aware of the breach on Tuesday, June 26, when it learned that an unauthorized party was claiming to have acquired the details of Adidas customers. The company said it’s still investigating the breach with law enforcement and security firms. The sportswear company did not include a tally of affected customers, but some news outlets like CBS, the Wall Street Journal, and Bloomberg reported citing inside sources that ‘a few millions’ of Adidas customers might be impacted.
…DBGer Ransomware Uses EternalBlue and Mimikats to Spread Across Networks
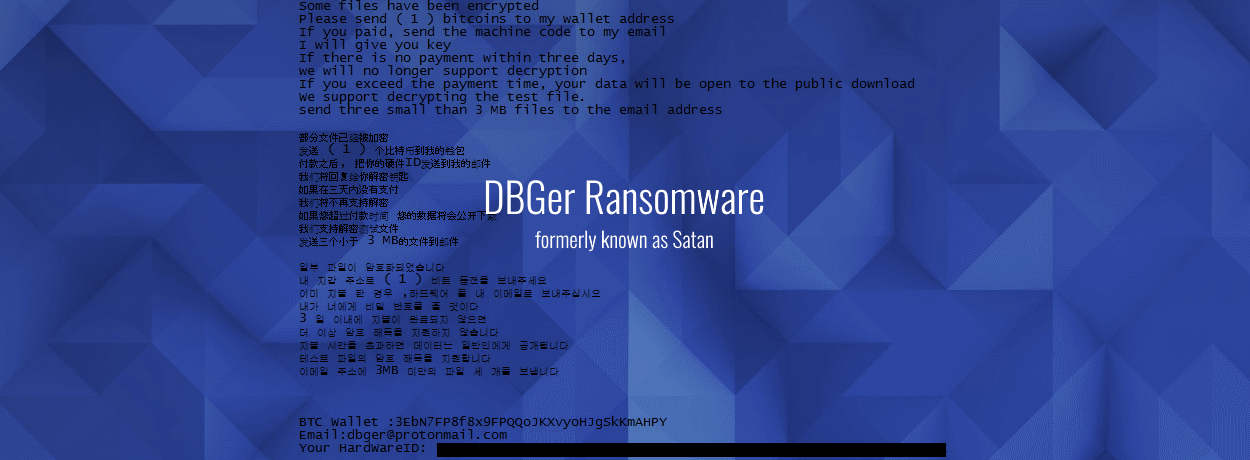
The change was not only in name but also in the ransomware’s modus operandi. According to the researcher, whose discovery was later confirmed by an Intezer code similarity analysis, the new (Satan) DBGer ransomware now also incorporates Mimikatz, an open-source password-dumping utility. The purpose of DBGer incorporating Mimikatz is for lateral movement inside compromised networks.
This fits a recently observed trend in Satan’s modus operandi. The Satan ransomware launched in January 2017 as a Ransomware-as-a-Service (RaaS) portal, allowing anyone to register and create custom versions of the Satan ransomware. First versions were unsophisticated, as most new ransomware variants tend to be.
…SEC announces cryptocurrency ether is not a security

Are bitcoin and ether securities? Finally, one of the biggest questions and debates in crypto has been answered by the SEC, officially. In an announcement at Yahoo Finance’s All Market Summit: Crypto in San Francisco on Thursday,the U.S. Securities and Exchange Commission Director of Corporate Finance William Hinman said that the commission would not be classifying ether or bitcoin as securities.
The commission’s policy is in line with what SEC Chair Jay Clayton said recently about bitcoin: that cryptocurrencies are not securities and the definition of “security” would not change to include bitcoin. (Clayton said digital tokens were securities, but cryptocurrencies were not.) Hinman’s announcement marks the official position of the SEC: the name isn’t important, but the way in which it’s sold, promised, and behaves is the key deciding factor.
…Malicious Docker Containers Earn Cryptomining Criminals $90K

Seventeen malicious Docker containers earned cryptomining criminals $90,000 in 30 days in what could be a harbinger of things to come. The figure may seem tame compared to some of the larger paydays that cryptojackers have earned. But, researchers at Kromtech Security Center warn containers are shaping up to be the next ripe target for these types of criminals.
Kromtech said the malicious Docker images (17 in total) were pulled down from the Docker Hub image repository. Researchers can’t say for sure how many times the rogue containers were used by Docker Hub users, but Kromtech estimates that the 17 images were downloaded collectively 5 million times during the year they were available. All 17 were removed from Docker Hub on May 10 by Docker, afterFortinetfound the containers and published a report on the images being used to mine cryptocurrency.
…17 Backdoored Docker Images Removed From Docker Hub

The Docker team has pulled 17 Docker container images that have been backdoored and used to install reverse shells and cryptocurrency miners on users’ servers for the past year. The malicious Docker container images have been uploaded on Docker Hub, the official repository of ready-made Docker images that sysadmins can pull and use on their servers, work, or personal computers. These Docker images allow sysadmins to quickly start an application container within seconds, without having to create their own Docker app container, a complicated and painstaking process that not all users are technically capable or inclined to do.
…MIT Device Uses WiFi to ‘See’ Through Walls and Track Your Movements
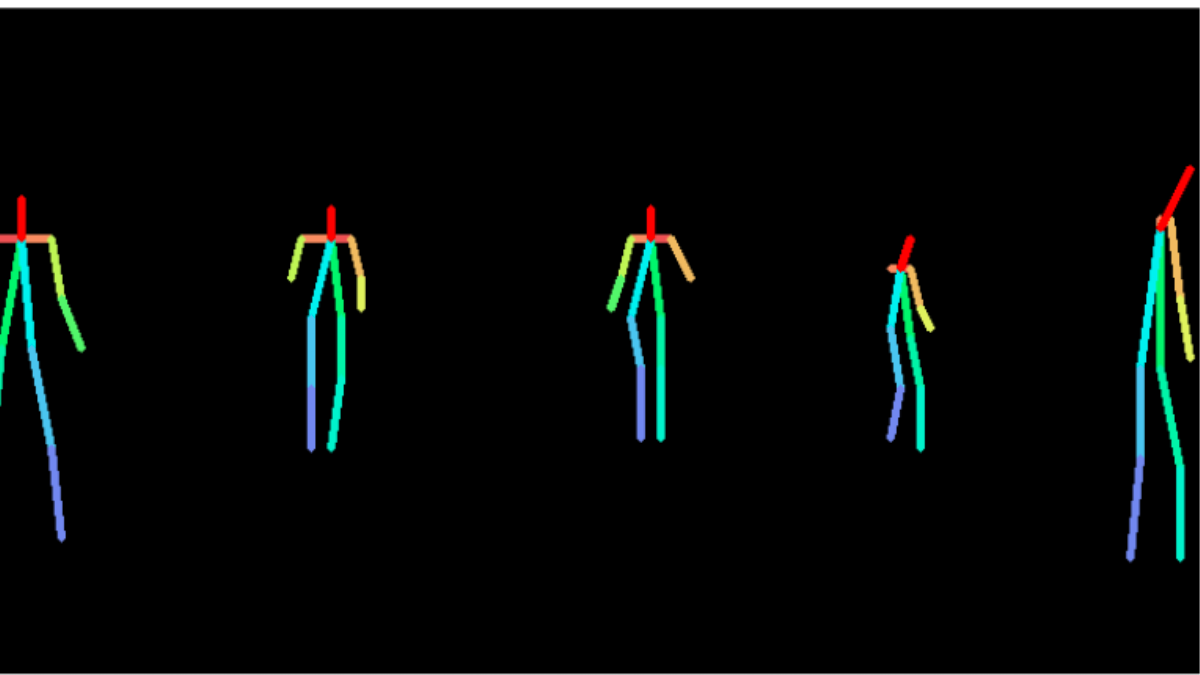
Anyone who has ever been intrigued by ads for x-ray specs in the back of a comic book will appreciate the latest work out of MIT, which advances technology to “see” through walls. Using WiFi, a team at Computer Science and Artificial Intelligence Laboratory (CSAIL) is now able to “see” a person on the other side of a wall and precisely track their movements, even if it’s something as subtle as giving a high five, according to new research to be presented at the Conference on Computer Vision and Pattern Recognition next week. Katabi told me that previous versions of the technology developed by her team were table to give you the position of the person and kind of their vague, blob-like outline, but not precise movements.
…