Sep. 14, 2019

The Russia-linked hackers who triggered a power outage in Ukraine back in 2016 may have hoped to cause much more damage, according to a report published recently by U.S.-based industrial cybersecurity firm Dragos. The threat group, which Dragos tracks as Electrum, used a piece of malware named Crashoverride and Industroyer to target industrial control systems (ICS) at a power station in Ukraine. The cyberattack resulted in power outages in the Kiev region in mid-December 2016, but power was restored after just over an hour, making the attack less severe compared to the one launched against Ukraine’s grid one year earlier, when power outages lasted for up to 6 hours.
Aug. 18, 2019

An Israeli company licenses software around the world that can crack just about any smartphone, but is its use always on the side of good? CEO of Israeli spyware-maker NSO on fighting terror, Khashoggi murder, and Saudi Arabia An Israeli company licenses software around the world that can crack just about any smartphone, but is its use always on the side of good?
Aug. 11, 2019

It looks like an Apple lightning cable. It works like an Apple lightning cable. But it will give an attacker a way to remotely tap into your computer.
I plugged the Apple lightning cable into my iPod and connected it to my Mac, just as I normally would. My iPod started charging, iTunes detected the device, and my iPod produced the pop-up asking if I wanted to trust this computer. All expected behaviour.
Jun. 28, 2019

When it comes to synchronizing large and important networks, for instance in the energy or financial sectors, every microsecond counts. Different protocols have been designed and implemented to achieve such precision. One of the most effective approaches is called IEEE 1588-2008 or the Precision Time Protocol (PTP).
But while PTP can in theory help networks synchronizetheir actions to within a microsecond, a team of computer scientists recently demonstrated that PTP also makes it possible—in multiple ways—to hack such a system. In a network using PTP, one central clock, referred to as a “master” clock, is responsible for coordinating and communicating time to “slave” clocks across the network (these controversial terms were recently removed fromthe popular programming language Python, but continue to be used in many fields). The master clock accomplishes this by sending time-stamped data packets to the slaves.
Nov. 14, 2018

Google lost control of several million of its IP addresses for more than an hour on Monday in an event that intermittently made its search and other services unavailable to many users and also caused problems for Spotify and other Google cloud customers. While Google said it had no reason to believe the mishap was a malicious hijacking attempt, the leak appeared suspicious to many, in part because it misdirected traffic to China Telecom, the Chinese government-owned provider that was recently caught improperly routing traffic belonging to a raft of Western carriers though mainland China. Further ReadingStrange snafu misroutes domestic US Internet traffic through China TelecomThe leak started at 21:13 UTC when MainOne Cable Company, a small ISP in Lagos, Nigeria, suddenly updated tables in the Internet’s global routing system to improperly declare that its autonomous system 37282 was the proper path to reach 212 IP prefixes belonging to Google.
Nov. 14, 2018

A large chunk of the hijacked traffic passed through the network of a controversial Chinese state-owned telecom provider that was previously accused of intentionally misdirecting internet traffic. A tiny Nigerian ISP has hijacked internet traffic meant for Google’s data centers. The incident, called a BGP hijack, occurred yesterday, on November 12, between 13:12 and 14:35, Pacific time, according to Google.
The incident was first detected and reported by BGPmon, an online service that monitors the routes that internet traffic takes through the smaller internet service provider (ISP) networks that make up the larger internet. According to BGPmon, the incident was caused by a small Nigerian ISP named MainOne Cable Company (AS37282), which announced to nearby ISPs that it was hosting IP addresses that were normally assigned to Google’s data center network. BGPmon says the Nigerian ISP incorrectly announced it was hosting 212 Google network prefixes in five different waves, for a total of 74 minutes.
Oct. 27, 2018

A Chinese state-owned telecommunications company has been ‘hijacking the vital internet backbone of western countries,’ according to an academic paper published this week by researchers from the US Naval War College and Tel Aviv University. The culprit is China Telecom, the country’s third-largest telco and internet service provider (ISP), which has had a presence inside North American networks since the early 2000s when it created its first point-of-presence (PoP). PoPs are data centers that do nothing more than re-route traffic between all the smaller networks that make up the larger internet.
Oct. 4, 2018

In 2015, Amazon.com Inc. began quietly evaluating a startup called Elemental Technologies, a potential acquisition to help with a major expansion of its streaming video service, known today as Amazon Prime Video. Based in Portland, Ore., Elemental made software for compressing massive video files and formatting them for different devices. Its technology had helped stream the Olympic Games online, communicate with the International Space Station, and funnel drone footage to the Central Intelligence Agency.
May. 23, 2018

After 13 months of research, the team discovered 14 vulnerabilities which could place connected cars at risk of compromise. The tests were conducted with BMW’s backing and in laboratory conditions. Impacted vehicles are included in the automaker’s i Series, X1 sDrive, 5 Series, and 7 Series.
In total, as documented in Keen Security Lab’s technical report (.PDF), nine of the attack scenarios presented required physical access to the target vehicle, while five were based on using a mobile Internet connection. The vulnerabilities permitted attackers to access the head unit — otherwise known as the infotainment system — and T-box components including the Telematics Control Unit and Central Gateway Module of the vehicles involved in the tests, leading to the creation and deployment of exploit chains designed to seize control of CAN buses. The exposure of CAN buses to attack is a serious issue considering that these buses connect all of a car’s functions.
May. 18, 2018

Car hacking has become a major focus in the security community in recent years, as more vehicles are hooked up to the cellular internet. But while convenient to control your car from your phone, it’s also opened up new points for attack — which could have real-world consequences. You might not even realize you’re a Calamp user.
Many apps, including the vehicle tracking app Viper SmartStart, which lets users locate, start, and control their car from their phone, connects to the outside world using a Calamp modem to its cloud-based servers. The researchers found that the Viper mobile app, while secure, was connecting to two different servers — one used by Viper, and another run by Calamp. Using the same credentials as the app, the researchers were also able to log in and gain complete access to the Calamp server, the researchers said in their write-up.
May. 17, 2018

Last week, Motherboard reported that a vigilante hacker had stolen data from a hacking group that researchers say is a government-linked cyberespionage unit. The data included GPS locations, text messages, and phone calls that the group had taken from their own victims. Now, that hacker has seemingly published the stolen data online for anyone to download.
The act itself highlights not only the fact that government hackers can sometimes face retribution, but also the ethical issues that come along with releasing such data to the public. The stolen files were seemingly from a server controlled by the so-called ZooPark group, a hacking outfit that cybersecurity researchers from Kaspersky revealed earlier this month in a report. At the time of the breach, Motherboard cross-referenced the stolen material with details in that Kaspersky report to corroborate the ZooPark link.
May. 15, 2018

Hackers—apparently working for the Turkish government— attempted to infect a large number of Turkish dissidents and protesters by spreading spyware on Twitter, according to a new report by digital rights organization Access Now. The organization’s researchers found seven new samples of spyware made by the infamous surveillance tech vendor FinFisher. One of them targeted several Turkish protesters who attended a large series of protests against the government of Recep Tayyip Erdoğan in June and July 2017, known as the March for Justice, according to the report.
May. 10, 2018

Somewhere, government-linked hackers might be panicking. A digital vigilante has struck back against what researchers believe is a cyberespionage group connected to a nation state. The hacker has allegedly stolen, rather ironically, a cache of data that the government-linked hackers lifted from their own victims across the Middle East.
The news provides a rare instance of someone targeting a so-called advanced persistent threat, or APT, as well as an opportunity for a behind-the-scenes look at a government hacking campaign. “10 minutes of effort; intel on Iranian APTs,” the anonymous hacker told Motherboard in an online chat, saying which nation they believe may be linked to the hacking group. Some cybersecurity experts tentatively agreed.
May. 6, 2018
Researchers said Chinese intelligence officers are behind almost a decade’s worth of network intrusions that use advanced malware to penetrate software and gaming companies in the US, Europe, Russia, and elsewhere. The hackers have struck as recently as March in a campaign that used phishing emails in an attempt to access corporate-sensitive Office 365 and Gmail accounts. In the process, they made serious operational security errors that revealed key information about their targets and possible location.
May. 3, 2018
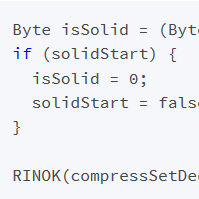
Very abstractly, the bug can be described as follows: The initialization of some member data structures of the RAR decoder classes relies on the RAR handler to configure the decoder correctly before decoding something. Unfortunately, the RAR handler fails to sanitize its input data and passes the incorrect configuration into the decoder, causing usage of uninitialized memory.
Source: landave.io
May. 1, 2018

Konrads Voits of Ypsilanti, Michigan, has been sentenced to seven years and three months in prison for attempting to hack the Washtenaw County Jail computer system and modifying prison records to get his friend released early. Besides spending 87 months in prison, Voits has also been ordered to pay $235,488 in fine to Washtenaw County for the cost accrued in investigating and cleaning up the infiltration that resulted in the compromise of personal information of around 1,600 employees, the US Justice Department announced last week.
Apr. 30, 2018

Without further ado, I present the first home(garage)made lithographically-fabricated integrated circuit – the “Z1” PMOS dual differential amplifier chip. I say “lithographically-fabricated” becauseJeri Ellsworth made the first transistors and logic gates (meticulously hand wired with conductive epoxy) andshowedthe world that this is possible. Inspired by her work, I have demonstratedICsmade by a scalable, industry-standard, photolithographic process.
Needless to say, this is the logical step-up from my previous replication of Jeri’s FET fabrication work.
Apr. 27, 2018

These days, companies in charge of some of the United States’ most critical infrastructure hire WhiteScope, Rios’s cybersecurity firm, to breach systems and then explain how they did it, all to prepare for the real thing. He and his team of researchers have picked apart the communication systems used by airplanes and cars. But sometimes Rios’s tests stray into unforeseen territory.
Apr. 26, 2018

The startup is called Crowdfense and is based in the United Arab Emirates. In an unusual move in the normally secretive industry of so-called zero-days, Crowdfense sent out a press release to reporters on Tuesday, advertising what it calls a bug bounty.
Source: vice.com
Apr. 26, 2018

Any key card will do. Even old and expired, or discarded keys retain enough residual data to be used in the attack. Using a handheld device running custom software, the researchers can steal data off of a key card — either using wireless radio-frequency identification (RFID) or the magnetic stripe.
That device then manipulates the stolen key data, which identifies the hotel, to produce an access token with the highest level of privileges, effectively serving as a master key to every room in the building.



















